Facebook Ads Direct Users to Fraudulent Websites That Steal Credit Card Information
Facebook users are falling victim to a scam e-commerce network that employs numerous fake websites to steal personal and financial information through brand impersonation and deceptive advertising tactics.
The Payment Fraud Intelligence team at Recorded Future, which identified the scam on April 17, 2024, has named the operation ERIAKOS, after the content delivery network (CDN) oss.eriakos[.]com used by the scammers.
“These fraudulent sites were designed to be accessed only through mobile devices and advertisements, a strategy to avoid automated detection systems,” the company explained. The network includes 608 fake websites and has operated in several short-lived waves.
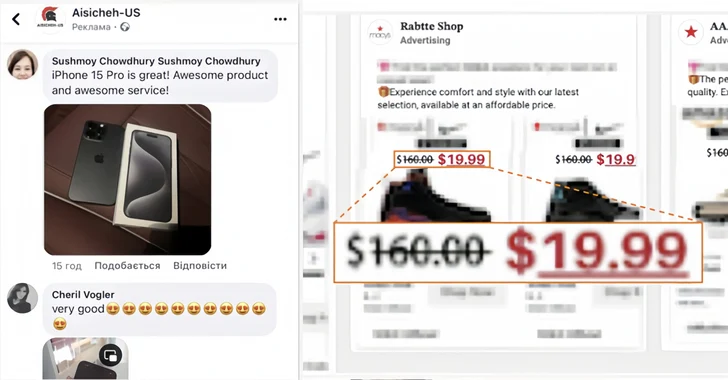
A key feature of this sophisticated scam is its exclusive targeting of mobile users who are lured to the fraudulent sites via Facebook ads, often featuring limited-time discounts to attract clicks. Recorded Future noted that up to 100 Meta Ads for a single scam website could be served in a single day.
The fake sites and ads mainly impersonate a major online shopping platform and a power tools manufacturer, as well as trick victims with false sales offers for products from well-known brands. Additionally, fake user comments on Facebook are used to attract potential victims.
“Merchant accounts and domains associated with the scam are registered in China, suggesting that the threat actors managing these accounts are likely based there,” Recorded Future reported.
This isn’t the first instance of criminal e-commerce networks targeting credit card information. In May 2024, a large network of 75,000 fake online stores, known as BogusBazaar, was found to have generated over $50 million through fake orders for brand-name shoes and apparel.
Last month, Orange Cyberdefense revealed a new traffic direction system (TDS) called R0bl0ch0n TDS, which promotes affiliate marketing scams via fake shop and sweepstake survey sites to collect credit card details.
“Multiple methods are used to initially spread URLs that redirect through the R0bl0ch0n TDS, indicating that different affiliates likely manage these campaigns,” said security researcher Simon Vernin.
Additionally, fake Google ads for Google Authenticator have been found to redirect users to a rogue site (“chromeweb-authenticators[.]com”), which hosts a Windows executable on GitHub that installs the DeerStealer information stealer.
These ads appear legitimate, as they are displayed as coming from “google.com,” with the advertiser’s identity verified by Google. Malwarebytes noted that someone has managed to impersonate Google and distribute malware disguised as a Google product.
Malvertising campaigns have also been observed spreading various other malware families, such as SocGholish (also known as FakeUpdates), MadMxShell, and WorkersDevBackdoor. Malwarebytes discovered infrastructure overlaps between MadMxShell and WorkersDevBackdoor, suggesting they are operated by the same threat actors.
Moreover, ads for Angry IP Scanner have been used to lure users to fake websites, and the email address “goodgoo1ge@protonmail[.]com” has been used to register domains serving MadMxShell and WorkersDevBackdoor.
“Both malware types are capable of stealing sensitive data and providing initial access to brokers involved in ransomware attacks,” said security researcher Jerome Segura.