Qilin Ransomware Attack Exploits VPN Credentials and Steals Chrome Data

The threat actors behind a recent Qilin ransomware attack have stolen credentials stored in Google Chrome on a select number of compromised systems.
This combination of credential theft alongside a ransomware attack introduces a rare and potentially far-reaching twist, according to a report from cybersecurity firm Sophos released on Thursday.
The attack, which was detected in July 2024, began when the attackers gained access to the target network using compromised VPN credentials for a portal that did not have multi-factor authentication (MFA). The attackers waited 18 days after the initial breach before taking further action.
Once inside the network, the attackers targeted the domain controller and modified the default domain policy to introduce a logon-based Group Policy Object (GPO) containing two elements, according to researchers Lee Kirkpatrick, Paul Jacobs, Harshal Gosalia, and Robert Weiland.
The first element was a PowerShell script called “IPScanner.ps1,” designed to extract credential data stored in the Chrome browser. The second was a batch script (“logon.bat”) that executed the first script upon user logon.
The GPO was left active on the network for over three days, providing ample time for users to unknowingly trigger the credential-harvesting script each time they logged in. The attackers then exfiltrated the stolen credentials and deleted evidence of their activity before encrypting files and leaving a ransom note in each directory.
The theft of Chrome-stored credentials now requires affected users to change their login information for all third-party sites.
“Ransomware groups continue to evolve their tactics, adding new techniques to their arsenal,” the researchers noted.
“If ransomware actors or others begin regularly mining endpoint-stored credentials—gaining access to subsequent targets or gathering valuable information about high-profile individuals for future exploitation—it could mark a troubling new phase in cybercrime.”
Emerging Ransomware Trends
This attack is part of a broader trend where ransomware groups like Mad Liberator and Mimic have been using unconventional methods such as unsolicited AnyDesk requests for data exfiltration and exploiting exposed Microsoft SQL servers for initial access.
In the Mad Liberator attacks, threat actors have been using this access to transfer and execute a binary named “Microsoft Windows Update.” This program displays a fake Windows Update splash screen, giving the victim the impression that legitimate updates are being installed, while the attackers secretly steal data.
The use of legitimate remote desktop tools instead of custom-made malware allows attackers to blend their activities with regular network traffic, making their actions harder to detect.
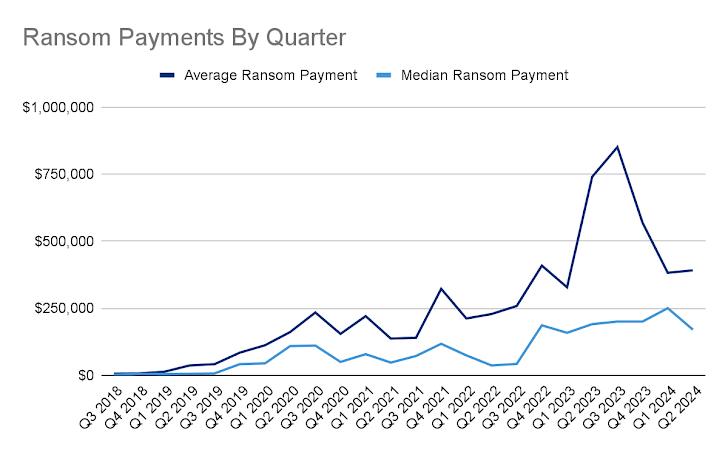
Despite numerous law enforcement actions, ransomware remains a highly profitable endeavor for cybercriminals, with 2024 on track to become the most lucrative year yet. This year also witnessed the largest ransomware payment ever recorded—approximately $75 million—paid to the Dark Angels ransomware group.
“The median ransom payment for the most severe ransomware strains surged from just under $200,000 in early 2023 to $1.5 million by mid-June 2024,” reported blockchain analytics firm Chainalysis. “This indicates that these strains are increasingly targeting larger businesses and critical infrastructure providers, which may be more likely to pay substantial ransoms due to their financial resources and essential roles.”
Ransomware victims are estimated to have paid $459.8 million to cybercriminals in the first half of 2024, up from $449.1 million during the same period last year. However, the total number of ransomware payment incidents recorded on the blockchain decreased by 27.29% year-over-year, suggesting a decline in the rate of payments.
Additionally, Russian-speaking threat groups were responsible for at least 69% of all cryptocurrency earnings linked to ransomware in the previous year, amounting to over $500 million.
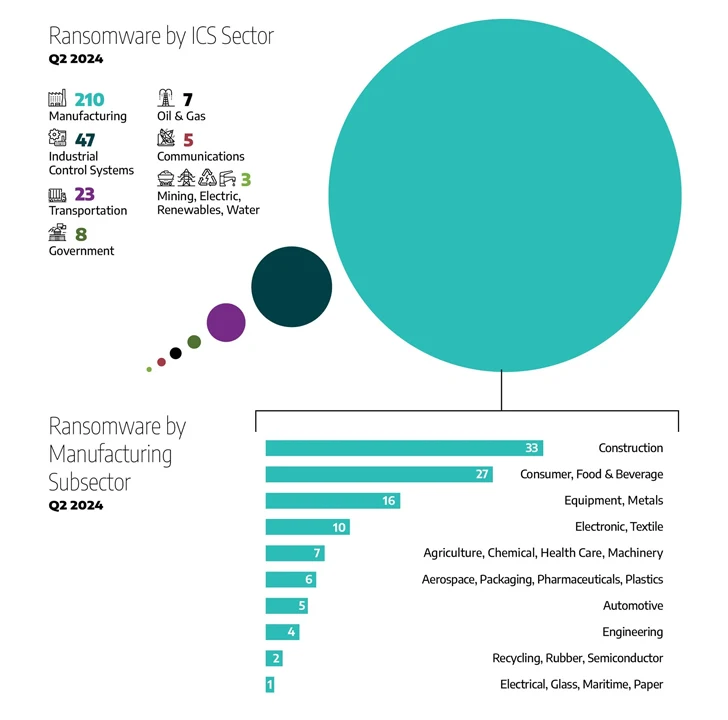
According to data from NCC Group, the number of ransomware attacks observed in July 2024 increased from 331 to 395 month-over-month but decreased from 502 reported during the same time last year. The most active ransomware groups included RansomHub, LockBit, and Akira. The most frequently targeted sectors were industrials, consumer cyclicals, and the hospitality and entertainment industries.
Industrial organizations are particularly attractive targets for ransomware attackers due to the critical nature of their operations and the significant impact of disruptions, which increases the likelihood that victims will pay the demanded ransom.
“Criminals target areas where they can create significant pain and disruption, aiming to prompt public demand for swift resolutions and, ideally, ransom payments to restore services quickly,” explained Chester Wisniewski, global field chief technology officer at Sophos.
“This makes utilities particularly attractive targets for ransomware attacks. Given their critical role in society, there’s a strong expectation for them to recover promptly with minimal disruption.”
Ransomware incidents in the utilities sector nearly doubled in Q2 2024 compared to Q1, rising from 169 to 312, according to Dragos. Most of these attacks were focused on North America (187), followed by Europe (82), Asia (29), and South America (6).
“Ransomware attackers are increasingly timing their strikes to coincide with peak holiday periods in some regions to maximize disruption and pressure organizations into paying ransoms,” noted NCC Group.
In its 2024 State of Ransomware report, Malwarebytes identified three key trends in ransomware tactics over the past year: a rise in attacks during weekends and early morning hours between 1 a.m. and 5 a.m., and a reduction in the time between initial access and encryption.
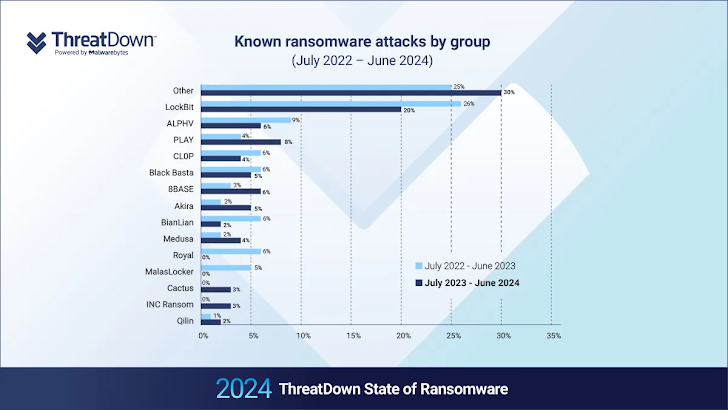
According to WithSecure, there has been a notable increase in the exploitation of edge services and targeting of small and medium-sized businesses. The dismantling of major ransomware groups like LockBit and ALPHV (also known as BlackCat) has undermined trust within the cybercriminal community, prompting affiliates to move away from these well-known brands.
Coveware reported that over 10% of the incidents they managed in Q2 2024 were unaffiliated, meaning they were carried out by attackers operating independently of any major ransomware group, often referred to as “lone wolves.”
Europol, in a recent assessment, noted that ongoing takedowns of cybercriminal forums and marketplaces have shortened the lifespan of these sites, as administrators seek to avoid attracting law enforcement attention. This uncertainty, coupled with a rise in exit scams, has led to the continued fragmentation of criminal marketplaces. Recent law enforcement actions and the release of ransomware source codes (such as Conti, LockBit, and HelloKitty) have further fragmented active ransomware groups and the variants they use.