New macOS Malware “Cthulhu Stealer” Targets Data of Apple Users

Cybersecurity researchers have discovered a new information-stealing malware targeting macOS systems, highlighting a growing focus on Apple’s operating system by threat actors.
Named Cthulhu Stealer, this malware has been offered through a malware-as-a-service (MaaS) model for $500 per month since late 2023. It is designed to target both x86_64 and ARM architectures.
According to Cado Security researcher Tara Gould, “Cthulhu Stealer is distributed as an Apple disk image (DMG) that includes two different binaries depending on the architecture. The malware, written in Golang, masquerades as legitimate software.”
The malware pretends to be various programs, including CleanMyMac, Grand Theft Auto IV, and Adobe GenP—a tool used to patch Adobe applications and bypass Creative Cloud activation.
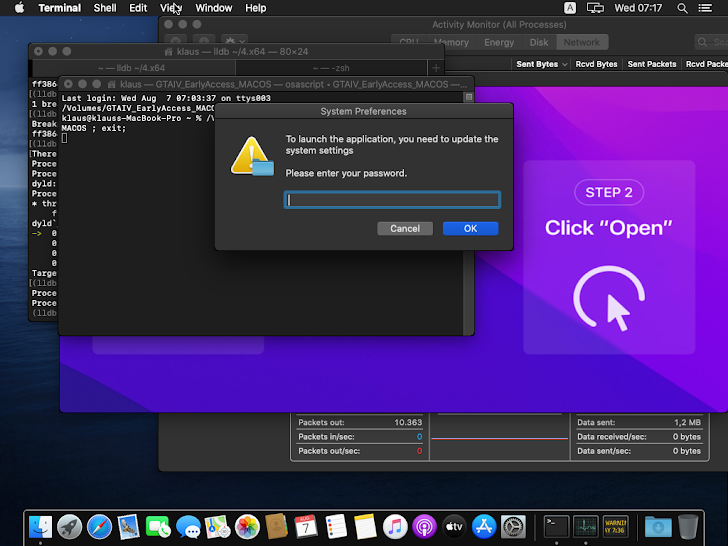
Users who run the unsigned file after manually overriding Gatekeeper protections are prompted to enter their system password through an osascript-based method, similar to techniques used by Atomic Stealer, Cuckoo, MacStealer, and Banshee Stealer.
Following this, a second prompt asks for the MetaMask password. Cthulhu Stealer also collects system information and dumps iCloud Keychain passwords using the open-source tool Chainbreaker.
The stolen data, including web browser cookies and Telegram account details, is then compressed into a ZIP archive and sent to a command-and-control (C2) server.
“The primary function of Cthulhu Stealer is to extract credentials and cryptocurrency wallets from various sources, including gaming accounts,” Gould explained.
“The features and behavior of Cthulhu Stealer closely resemble those of Atomic Stealer, suggesting that the developer likely adapted Atomic Stealer’s code. The use of osascript to request user passwords is similar in both malware types, even sharing identical spelling errors.”
The developers behind Cthulhu Stealer are reportedly inactive now, partly due to disputes over payments and accusations of exit scams by affiliates. This has led to the main developer being permanently banned from a cybercrime marketplace where the stealer was advertised.
Cthulhu Stealer itself is not particularly advanced and lacks anti-analysis measures that might help it evade detection. It also does not offer any unique features that set it apart from other similar malware in the underground market.
While macOS threats are less common than those targeting Windows and Linux, users are advised to download software only from reputable sources, avoid installing unverified applications, and keep their systems updated with the latest security patches.
Apple has recognized the rise in macOS malware and has responded by introducing new security measures in its upcoming operating system version. In macOS Sequoia, users will no longer be able to bypass Gatekeeper by Control-clicking on software that isn’t properly signed or notarized. Instead, they will need to navigate to System Settings > Privacy & Security to review and approve such software.