“‘Stargazer Goblin’ Generates 3,000 Fake GitHub Accounts to Distribute Malware”

A threat actor known as Stargazer Goblin has established a network of fake GitHub accounts to support a Distribution-as-a-Service (DaaS) operation, spreading various types of information-stealing malware and earning $100,000 in illicit profits over the past year.
This network consists of over 3,000 accounts on GitHub, distributing malware through thousands of repositories, according to Check Point, which has named it “Stargazers Ghost Network.”
Malware families propagated using this method include Atlantida Stealer, Rhadamanthys, RisePro, Lumma Stealer, and RedLine. The fake accounts engage in activities like starring, forking, watching, and subscribing to malicious repositories to give them a semblance of legitimacy.
The network is believed to have been active since August 2022 in some form, though an advertisement for the DaaS was only noticed in early July 2023.
“Threat actors now operate a network of ‘Ghost’ accounts that distribute malware via malicious links on their repositories and encrypted archives as releases,” security researcher Antonis Terefos explained in an analysis published last week.
“This network not only distributes malware but also engages in activities that make these ‘Ghost’ accounts appear as regular users, lending fake legitimacy to their actions and the associated repositories.”
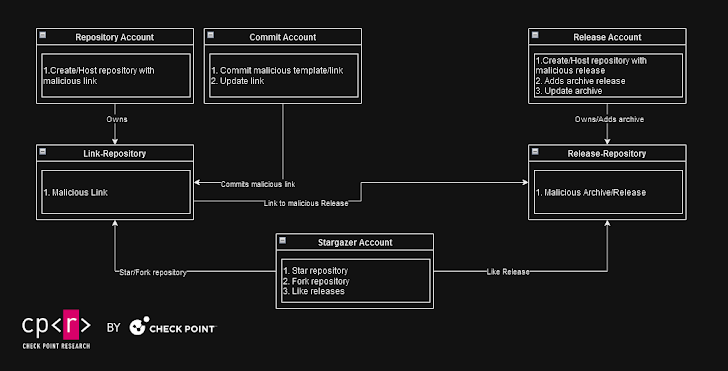
Different categories of GitHub accounts are responsible for various aspects of the scheme to make their infrastructure more resilient to takedown efforts by GitHub when malicious payloads are flagged on the platform.
These include accounts that serve the phishing repository template, accounts providing the image for the phishing template, and accounts that push malware to the repositories as a password-protected archive disguised as cracked software and game cheats.
If the third set of accounts is detected and banned by GitHub, Stargazer Goblin updates the first account’s phishing repository with a new link to an active malicious release, allowing the operators to continue with minimal disruption.
Besides liking new releases from multiple repositories and committing changes to README.md files to modify the download links, evidence suggests that some accounts in the network have been previously compromised, with credentials likely obtained via stealer malware.
“Most of the time, we observe that Repository and Stargazer accounts remain unaffected by bans and repository takedowns, whereas Commit and Release accounts are typically banned once their malicious repositories are detected,” Terefos said.
“It’s common to find Link-Repositories containing links to banned Release-Repositories. When this occurs, the Commit account associated with the Link-Repository updates the malicious link with a new one.”
One of the campaigns discovered by Check Point involves a malicious link to a GitHub repository that, in turn, points to a PHP script hosted on a WordPress site and delivers an HTML Application (HTA) file to execute Atlantida Stealer using a PowerShell script.
Other malware families propagated via the DaaS include Lumma Stealer, RedLine Stealer, Rhadamanthys, and RisePro. Check Point noted that the GitHub accounts are part of a larger DaaS solution that operates similar ghost accounts on platforms such as Discord, Facebook, Instagram, X, and YouTube.
“Stargazer Goblin has developed a highly sophisticated malware distribution network that leverages GitHub’s reputation as a legitimate website to evade detection, mask malicious activities, and swiftly recover from any disruptions caused by GitHub’s actions,” said Terefos.
“By employing multiple accounts with distinct roles, such as starring, hosting repositories, committing phishing templates, and releasing malicious files, the Stargazers Ghost Network can mitigate losses when GitHub intervenes. Typically, only one part of the network is affected rather than all associated accounts.”
This development coincides with unknown threat actors targeting GitHub repositories, wiping their contents, and demanding victims contact a user named Gitloker on Telegram as part of an extortion scheme ongoing since February 2024.
The social engineering attack involves phishing emails sent from “notifications@github.com,” tricking developers into clicking on fake links disguised as job opportunities at GitHub. Once clicked, they are prompted to authorize a new OAuth app, which then erases all repositories and demands a payment for their restoration.
Additionally, a recent advisory from Truffle Security highlighted the possibility of accessing sensitive data from deleted forks, deleted repositories, and even private repositories on GitHub. This vulnerability, termed Cross Fork Object Reference (CFOR), allows one repository fork to access data from another, including private and deleted forks.
“A CFOR vulnerability occurs when one repository fork can access sensitive data from another fork, including data from private and deleted forks,” explained Joe Leon. “Similar to an Insecure Direct Object Reference, in CFOR users supply commit hashes to directly access commit data that otherwise would not be visible to them.”
In essence, a piece of code committed to a public repository may be accessible indefinitely as long as at least one fork of that repository exists. Additionally, it could be used to access code committed during the time between an internal fork’s creation and the repository’s transition to public.
These are, however, intentional design decisions by GitHub, as noted in their documentation:
- Commits to any repository in a fork network can be accessed from any repository in the same network, including the upstream repository.
- When a private repository is made public, all commits, including those made in forked repositories, become visible to everyone.
“The average user perceives the separation of private and public repositories as a security boundary, believing that data in a private repository cannot be accessed by public users,” Leon said.
“Unfortunately, this is not always true. Moreover, deletion implies data destruction. As we’ve seen, deleting a repository or fork does not mean commit data is actually deleted.”