Iranian Hackers Unleash New BugSleep Backdoor in Cyber Attacks Across the Middle East
The Iranian nation-state group known as MuddyWater has been identified using a new backdoor in a recent attack campaign, deviating from its usual strategy of deploying legitimate remote monitoring and management (RMM) software for persistent access.
Independent reports from cybersecurity firms Check Point and Sekoia, which have named the malware strains BugSleep and MuddyRot respectively, reveal this new approach.
“In this campaign, MuddyWater altered their infection chain and did not utilize the legitimate Atera remote monitoring and management tool (RRM) as a validator,” Sekoia stated in a report shared with The Hacker News. “Instead, they employed a new and undocumented implant.”
Initial details of the campaign were disclosed by Israeli cybersecurity firm ClearSky on June 9, 2024. The targets include Turkey, Azerbaijan, Jordan, Saudi Arabia, Israel, and Portugal.
MuddyWater (also known as Boggy Serpens, Mango Sandstorm, and TA450) is believed to be linked to Iran’s Ministry of Intelligence and Security (MOIS).
The group’s cyber attacks typically involve spear-phishing emails to deliver various RMM tools like Atera Agent, RemoteUtilities, ScreenConnect, SimpleHelp, and Syncro.
In April, HarfangLab reported an increase in MuddyWater campaigns using Atera Agent since late October 2023, targeting businesses in Israel, India, Algeria, Turkey, Italy, and Egypt. The sectors affected include airlines, IT, telecoms, pharma, automotive manufacturing, logistics, travel, and tourism.
“MuddyWater prioritizes gaining access to business email accounts in their ongoing attack campaigns,” the French cybersecurity firm noted.
“These compromised accounts serve as valuable assets, allowing the group to enhance the credibility and effectiveness of their spear-phishing campaigns, maintain persistence within targeted organizations, and avoid detection by blending with legitimate network traffic.”
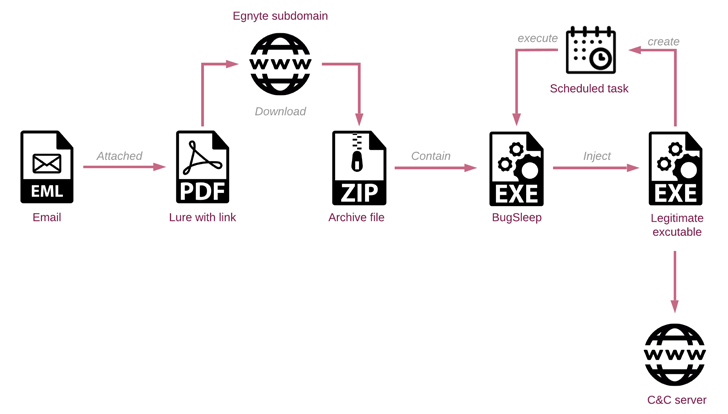
In the latest attack chains, compromised email accounts from legitimate companies are used to send spear-phishing messages containing either a direct link or a PDF attachment leading to an Egnyte subdomain. This subdomain has previously been exploited by the threat actor to distribute Atera Agent.
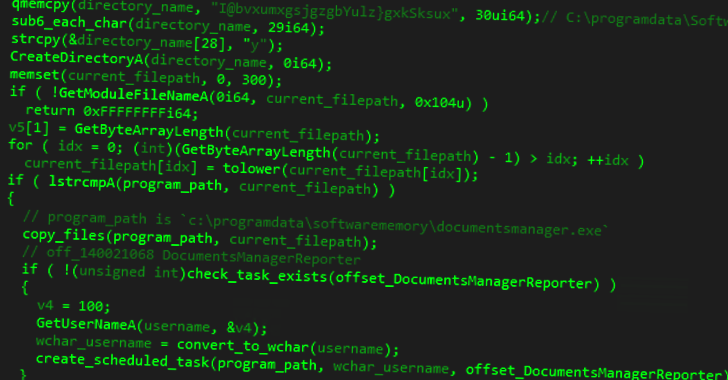
BugSleep, also known as MuddyRot, is an x64 implant developed in C, featuring capabilities to download/upload files, launch a reverse shell, and establish persistence. Communication with a command-and-control (C2) server occurs over a raw TCP socket on port 443.
“The first message sent to the C2 is the victim host fingerprint, which combines the hostname and the username separated by a slash,” Sekoia explained. “If the victim receives ‘-1,’ the program stops; otherwise, the malware enters an infinite loop, waiting for new orders from the C2.”
The reason behind MuddyWater’s switch to a custom implant remains unclear, though it is speculated that increased monitoring of RMM tools by security vendors might have influenced the decision.
“The increased activity of MuddyWater in the Middle East, particularly in Israel, underscores the persistent nature of these threat actors, who continue to target a wide variety of organizations in the region,” Check Point noted.
“Their consistent use of phishing campaigns, now enhanced with a custom backdoor, BugSleep, signifies a notable advancement in their techniques, tactics, and procedures (TTPs).”



