The Benefits and Risks of RMM Tools

As remote work becomes more prevalent, IT departments must manage devices spread across various cities and countries, relying on VPNs and remote monitoring and management (RMM) tools for system administration.
However, like any technology, RMM tools can be misused. Threat actors can exploit these tools to connect to a victim’s device, execute commands, exfiltrate data, and remain undetected.
This article will discuss real-world examples of RMM exploits and provide guidance on protecting your organization from such attacks.
What are RMM tools?
RMM software streamlines network management, enabling IT professionals to remotely resolve issues, install software, and transfer files to and from devices.
Unfortunately, these connections are not always secure, and attackers can use malicious software to link their servers to a victim’s device. As detection methods improve, ransomware-as-a-service (RaaS) groups have adapted their tactics.
In many of the cyber incidents investigated by Varonis last year, RaaS gangs employed a technique known as Living off the Land, using legitimate IT tools to gain remote control, move through networks undetected, and steal data.
RMM tools allow attackers to blend in and avoid detection, as their traffic is often “ignored” by security controls and organizational security policies, such as application whitelisting.
This strategy also aids less experienced attackers — once connected, they find everything they need already installed and ready to use.
Our research identified two primary methods attackers use to manipulate RMM tools:
- Abusing existing RMM tools: Attackers gain initial access to an organization’s network using preexisting RMM tools. They exploit weak or default credentials or tool vulnerabilities to gain access without triggering detection.
- Installing new RMM tools: Attackers install their preferred RMM tools by first gaining access to the network. They use phishing emails or social engineering techniques to trick victims into unwittingly installing the RMM tool on their network.
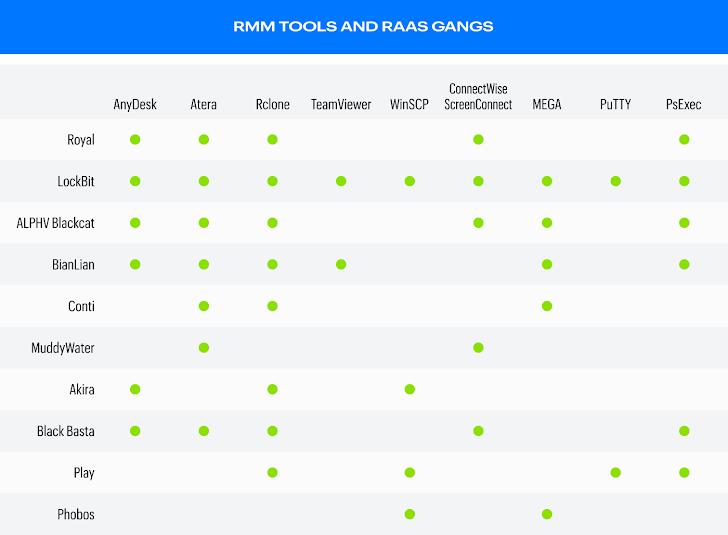
Below are common RMM tools and RaaS gangs:
Real-World Examples of RMM Exploits
In a recent case, our Managed Data Detection and Response (MDDR) team investigated a compromised device within an organization and discovered evidence of an RMM tool named “KiTTY” in the PowerShell history. KiTTY is a modified version of PuTTY, a widely used tool for telnet and SSH sessions.
Because PuTTY is a legitimate tool, the organization’s security systems did not flag KiTTY, allowing it to establish reverse tunnels over port 443 and expose internal servers to an AWS EC2 instance. The Varonis team’s thorough analysis revealed that the sessions to the AWS EC2 box using KiTTY were crucial in tracing the attack, identifying stolen files, and uncovering security vulnerabilities.
Strategies to Defend Against RMM Exploits
1. Implement an Application Control Policy
- Limit the use of RMM tools by enforcing strict application control policies. Ensure that RMM tools are up-to-date, patched, and accessible only to authorized users with multi-factor authentication (MFA).
- Block both inbound and outbound connections on restricted RMM ports and protocols at the network perimeter.
To enforce this, you can create a Windows Defender Application Control (WDAC) policy with PowerShell:
- Create a New Policy: Use the
New-CIPolicycmdlet to create a policy that allows applications based on their publisher. For instance: New-CIPolicy -FilePath “C:\Path\To\Application.exe” -Level Publisher -UserPEs -Fallback Hash -Enable -OutputFilePath “C:\Path\To\Policy.xml” - Convert the Policy to Binary Format: Convert the policy using the
ConvertFrom-CIPolicycmdlet: ConvertFrom-CIPolicy -XmlFilePath “C:\Path\To\Policy.xml” -BinaryFilePath “C:\Path\To\Policy.bin”
- Deploy the Policy: Deploy the binary policy file using Group Policy Management Console (GPMC) by copying the .bin file to
\\Windows\System32\CodeIntegrityon each relevant computer and configuring the policy settings in GPMC.
2. Continuous Monitoring
- Regularly monitor network traffic and logs, particularly related to RMM tools. Utilize services like Varonis MDDR for around-the-clock network monitoring and behavioral analysis.
3. User Training and Awareness
- Educate employees on recognizing phishing attempts and managing passwords. Encourage reporting of suspicious activities and regularly test the cybersecurity team to address potential vulnerabilities.
4. Data Risk Assessment
- Stay proactive with your security measures. Varonis offers a comprehensive Data Risk Assessment that provides immediate insights into potential risks in your environment. This free assessment delivers a detailed view of critical data and outlines automated remediation strategies within 24 hours.
For more information on assessing and enhancing your data security, consider scheduling a Varonis Data Risk Assessment today.