Chinese Hackers Target Japanese Companies with LODEINFO and NOOPDOOR Malware

Japanese organizations have become the target of a Chinese nation-state threat actor utilizing malware families such as LODEINFO and NOOPDOOR to steal sensitive information from compromised systems. In some cases, the attackers have managed to remain undetected for two to three years.
Israeli cybersecurity firm Cybereason has named this campaign Cuckoo Spear, linking it to the well-known intrusion group APT10, also referred to as Bronze Riverside, ChessMaster, Cicada, Cloudhopper, MenuPass, MirrorFace, Purple Typhoon (formerly Potassium), and Stone Panda.
According to Cybereason, “The actors behind NOOPDOOR not only employed LODEINFO during the campaign but also used the new backdoor to exfiltrate data from compromised enterprise networks.”
These revelations follow recent warnings from JPCERT/CC about cyberattacks by this threat actor against Japanese organizations using both malware strains.
In January, ITOCHU Cyber & Intelligence reported discovering an updated version of the LODEINFO backdoor with enhanced anti-analysis features, noting that spear-phishing emails were used to distribute the malware.
Trend Micro, which originally named the group MenuPass, describes APT10 as consisting of two clusters known as Earth Tengshe and Earth Kasha. This hacking group has been active since at least 2006.

Earth Tengshe is associated with campaigns deploying SigLoader and SodaMaster, while Earth Kasha is specifically linked to the use of LODEINFO and NOOPDOOR. Both sub-groups have been observed targeting public-facing applications with the intent to exfiltrate data and information within networks.
Earth Tengshe is also reportedly connected to another cluster known as Bronze Starlight (also referred to as Emperor Dragonfly or Storm-0401), which is known for operating short-lived ransomware families such as LockFile, Atom Silo, Rook, Night Sky, Pandora, and Cheerscrypt.
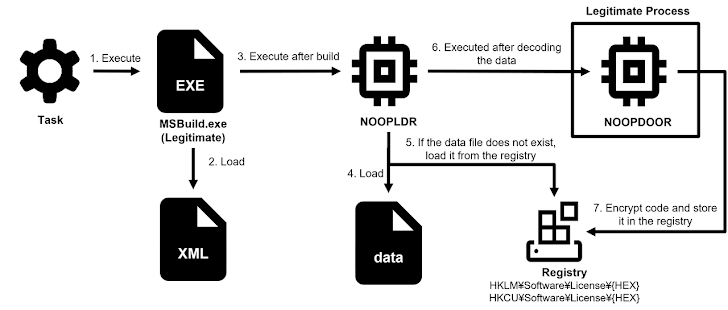
Conversely, Earth Kasha has adapted its initial access methods by exploiting public-facing applications since April 2023. This includes taking advantage of unpatched vulnerabilities in Array AG (CVE-2023-28461), Fortinet (CVE-2023-27997), and Proself (CVE-2023-45727) to deploy LODEINFO and NOOPDOOR (also known as HiddenFace).
LODEINFO is equipped with commands to execute arbitrary shellcode, log keystrokes, capture screenshots, terminate processes, and exfiltrate files to a server controlled by the attackers. NOOPDOOR, which shares code similarities with another APT10 backdoor named ANEL Loader, offers functionality to upload and download files, execute shellcode, and run additional programs.
“LODEINFO appears to serve as the primary backdoor, while NOOPDOOR functions as a secondary backdoor, ensuring persistent access within the compromised corporate network for over two years,” Cybereason noted. “The threat actors maintain their presence in the network by exploiting scheduled tasks.”