Apple Vision Pro Vulnerability Allowed Virtual Keyboard Inputs to Be Exposed to Attackers

A recently patched security flaw in Apple’s Vision Pro mixed reality headset has come to light, which, if exploited, could allow attackers to infer data typed on the device’s virtual keyboard.
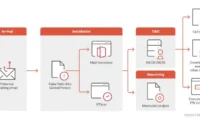
The attack, named GAZEploit and tracked as CVE-2024-40865, was discovered by researchers from the University of Florida, CertiK Skyfall Team, and Texas Tech University.
The researchers described it as a “novel attack that can infer eye-related biometrics from the avatar image to reconstruct text entered via gaze-controlled typing.” GAZEploit takes advantage of vulnerabilities in gaze-controlled text entry, particularly when users share a virtual avatar.
After responsible disclosure, Apple fixed the issue in visionOS 1.3, released on July 29, 2024. The vulnerability was tied to a component called Presence, which Apple stated could expose virtual keyboard inputs through the Persona avatar feature. To address the issue, Apple suspended Persona when the virtual keyboard is in use.
In essence, the researchers discovered that by analyzing a virtual avatar’s eye movements, attackers could determine what the user was typing, compromising privacy. This type of attack could potentially be used to extract sensitive information, such as passwords, during video calls, online meetings, or live streaming.
The attack works through a supervised learning model trained on Persona recordings, eye aspect ratio (EAR), and gaze estimation. It can differentiate between typing and other virtual reality activities, such as gaming or watching movies. By analyzing the eye movements, the model can map gaze directions to specific keys on the virtual keyboard, allowing for keystroke inference.
“By remotely capturing and analyzing the virtual avatar video, an attacker can reconstruct the typed keys,” the researchers noted, adding that GAZEploit is the first known attack to use leaked gaze data for remote keystroke inference.