Europol Dismantles Large-Scale Phishing Operation Targeting Mobile Phone Credentials

Law enforcement agencies have successfully dismantled an international criminal organization that operated a phishing platform used to unlock stolen or lost mobile phones.
The phishing-as-a-service (PhaaS) platform, known as iServer, is estimated to have affected over 483,000 victims worldwide, with the highest numbers reported in Chile (77,000), Colombia (70,000), Ecuador (42,000), Peru (41,500), Spain (30,000), and Argentina (29,000).
Europol, in an official statement, noted, “The victims are mainly Spanish-speaking nationals from countries in Europe, North America, and South America.”
This operation, named Operation Kaerb, involved the coordinated efforts of law enforcement and judicial agencies from Spain, Argentina, Chile, Colombia, Ecuador, and Peru.
As part of this joint action, carried out between September 10 and 17, an Argentinian individual responsible for creating and managing the PhaaS platform since 2018 has been arrested.
Overall, the operation resulted in 17 arrests, 28 searches, and the confiscation of 921 items, including mobile phones, electronic devices, vehicles, and weapons. It’s estimated that up to 1.2 million mobile phones have been unlocked using this platform.
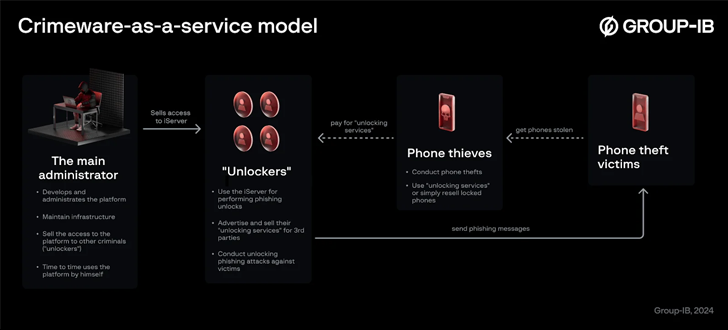
Group-IB, a cybersecurity firm, noted that while iServer operated as an automated phishing platform, its unique focus was on capturing credentials to unlock stolen devices, differentiating it from other phishing-as-a-service models.
The iServer platform, according to the Singapore-based company, provided a web interface that allowed criminals, known as “unlockers,” to extract device passwords and user credentials from cloud-based mobile platforms, enabling them to bypass security features like Lost Mode and unlock the devices.
The criminal organization’s administrator offered access to these unlockers, who then used iServer to not only perform phishing unlocks but also sell their services to third parties, such as phone thieves.
These unlockers were also responsible for sending fraudulent messages to victims of phone theft, aiming to collect data needed to access the stolen devices. This was often done by sending SMS messages that prompted recipients to locate their lost phone by clicking on a deceptive link.
This process initiates a redirection chain that eventually directs the victim to a fake landing page, where they are asked to input their login credentials, device passcode, and two-factor authentication (2FA) codes. These details are then exploited to gain unauthorized access to the device, disable Lost Mode, and disconnect the device from the owner’s account.
Group-IB noted, “iServer automates the generation and distribution of phishing pages that mimic well-known cloud-based mobile platforms, incorporating several unique features that increase its effectiveness as a tool for cybercriminals.”

Global Operation Takes Down Ghost Platform
Europol, in collaboration with the Australian Federal Police (AFP), has announced the takedown of an encrypted communication network known as Ghost (“www.ghostchat[.]net”), which was being used to facilitate organized crime on an international scale.
The platform was accessible through a custom Android smartphone, costing around $1,590 for a six-month subscription, and was utilized for a range of illegal activities, including drug trafficking, money laundering, and acts of extreme violence. This marks the latest in a series of similar takedowns of encrypted communication services such as Phantom Secure, EncroChat, Sky ECC, and Exclu.
According to Europol, “The solution employed three encryption standards and included a feature that allowed users to send a specific code with a message, triggering the automatic deletion of all messages on the target device.” This capability enabled criminal groups to communicate securely, avoid detection, bypass forensic investigations, and manage their illegal activities across different countries.
It is estimated that several thousand individuals used the Ghost platform, with approximately 1,000 messages exchanged daily on the service before it was taken offline.
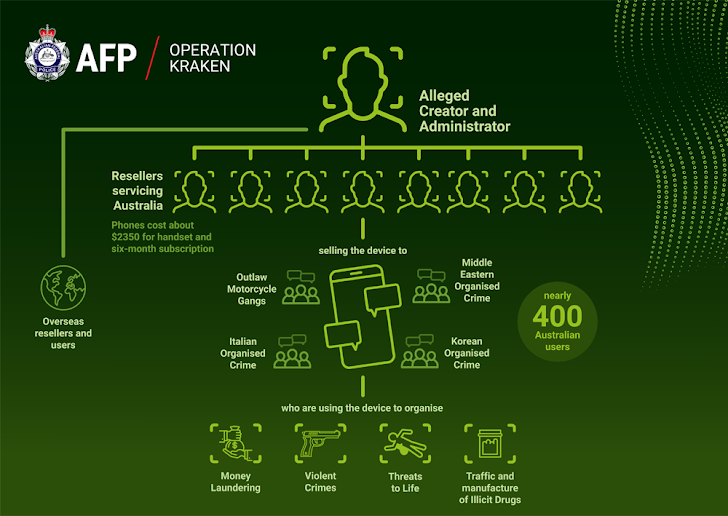
During an investigation that began in March 2022, authorities have arrested a total of 51 suspects: 38 in Australia, 11 in Ireland, one in Canada, and one in Italy, linked to the Italian Sacra Corona Unita mafia organization.
Among those apprehended is a 32-year-old man from Sydney, New South Wales, who has been charged with creating and managing the Ghost platform as part of Operation Kraken. Several other individuals have been accused of using the platform for trafficking cocaine and cannabis, drug distribution, and fabricating a false terrorism plot.
The alleged administrator, Jay Je Yoon Jung, reportedly started this criminal venture nine years ago, amassing millions of dollars in illegal profits. He was arrested at his residence in Narwee. The operation also resulted in the dismantling of a drug lab in Australia and the seizure of weapons, drugs, and €1 million in cash.
The Australian Federal Police (AFP) revealed that it infiltrated the platform’s infrastructure by executing a software supply chain attack, altering the update process to gain access to data stored on 376 active devices in Australia.
Europol stated, “Recent law enforcement actions targeting platforms used by criminal networks have caused the encrypted communication landscape to become increasingly fragmented.” As a result, criminals are turning to less established or custom-built communication tools that offer varying degrees of security and anonymity, as well as using popular communication apps to diversify their methods.
Europol emphasized the importance of accessing suspect communications to combat serious crimes and urged private companies to prevent their platforms from becoming safe havens for criminals, while ensuring lawful data access with judicial oversight and respect for fundamental rights.
In a parallel effort, Germany has seized 47 cryptocurrency exchange services operating in the country that facilitated illegal money laundering for cybercriminals, including ransomware operators, darknet vendors, and botnet administrators. This operation, called Final Exchange, targeted services accused of not implementing Know Your Customer (KYC) or anti-money laundering protocols, allowing the concealment of illicit funds. The Federal Criminal Police Office (Bundeskriminalamt) stated that these services enabled anonymous cryptocurrency exchanges without requiring user registration or identity verification.
Additionally, the U.S. Department of Justice (DoJ) announced the arrest and charging of two individuals involved in a $230 million cryptocurrency scam. The suspects, Malone Lam, 20, and Jeandiel Serrano, 21, along with others, allegedly stole cryptocurrency from a victim in Washington D.C. since at least August 2024 by gaining access to victims’ accounts. The stolen funds were laundered through multiple exchanges and mixers, enabling the suspects to finance a lavish lifestyle, including luxury travel, automobiles, watches, designer handbags, and high-end rental properties.
The DoJ noted that the suspects laundered the proceeds by using various methods, including mixers, exchanges, “peel chains,” pass-through wallets, and virtual private networks (VPNs) to disguise their true identities.



