Hackers Spreading Malicious Python Packages Through Popular Developer Q&A Platform
In yet another indication that cybercriminals are constantly devising new methods to deceive users into downloading malware, it has been revealed that the Q&A platform Stack Exchange has been exploited to direct unsuspecting developers to fake Python packages designed to drain cryptocurrency wallets.
According to a report shared with The Hacker News by Checkmarx researchers Yehuda Gelb and Tzachi Zornstain, the malicious code embedded within these packages executes automatically upon installation, initiating a sequence of events aimed at compromising the victim’s systems, exfiltrating their data, and emptying their crypto wallets.
The campaign, which began on June 25, 2024, specifically targeted cryptocurrency users involved with Raydium and Solana. The following is a list of the rogue packages identified:
- raydium (762 downloads)
- raydium-sdk (137 downloads)
- sol-instruct (115 downloads)
- sol-structs (292 downloads)
- spl-types (776 downloads)
These packages, which have collectively been downloaded 2,082 times, are no longer available on the Python Package Index (PyPI) repository.
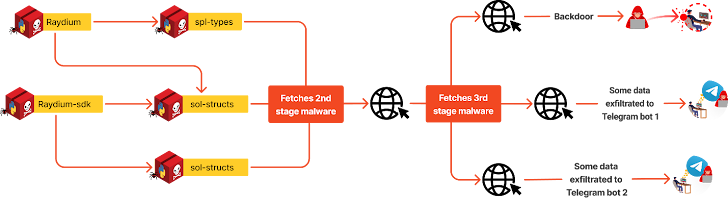
The malware hidden within these packages functioned as a comprehensive information stealer, targeting a wide range of data, including web browser passwords, cookies, credit card information, cryptocurrency wallets, and data from messaging apps such as Telegram, Signal, and Session.
In addition, the malware was equipped to take screenshots of the system and search for files containing GitHub recovery codes and BitLocker keys. The collected information was then compressed and transmitted to two Telegram bots controlled by the attackers.
Moreover, a backdoor component in the malware provided the attacker with persistent remote access to the victim’s machines, facilitating potential future exploitation and long-term system compromise.
The attack chain involved multiple stages, with the “raydium” package listing “spl-types” as a dependency to obscure its malicious intent and create the appearance of legitimacy.
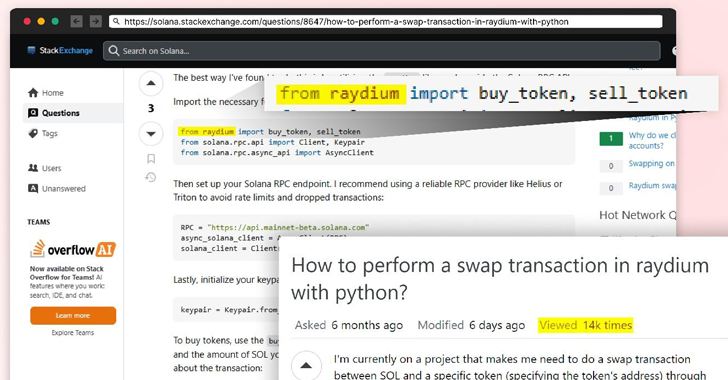
A noteworthy element of this campaign was the use of Stack Exchange as a means to promote adoption. The attackers posted seemingly helpful answers to developer questions about performing swap transactions in Raydium using Python, which referenced the malicious packages.
“The attacker strategically selected a highly visible thread with thousands of views to maximize their reach,” the researchers explained, noting that this was done to “add credibility to the package and encourage widespread adoption.”
Although the answer has since been removed from Stack Exchange, The Hacker News discovered a reference to “raydium” in an unanswered question on the platform dated July 9, 2024. The user wrote, “I have been struggling for nights to get a swap on the Solana network running in Python 3.10.2—installed Solana, Solders, and Raydium but can’t get it to work.”
Mentions of “raydium-sdk” also appeared in a post titled “How to Buy and Sell Tokens on Raydium using Python: A Step-by-Step Solana Guide,” which was shared on Medium by a user named SolanaScribe on June 29, 2024.
It’s unclear when the packages were removed from PyPI, as two other users recently commented on the Medium post, asking for help with installing “raydium-sdk” as recently as six days ago. Checkmarx informed The Hacker News that the post wasn’t authored by the threat actor.
This tactic is not new. In May, Sonatype reported a similar incident where a package named pytoileur was promoted through Stack Overflow, another Q&A service, to facilitate cryptocurrency theft.
This development underscores how attackers exploit the trust in community-driven platforms to distribute malware, leading to supply chain attacks on a large scale.
“A single compromised developer can unknowingly introduce vulnerabilities into an entire company’s software ecosystem, potentially impacting the entire corporate network,” the researchers emphasized. “This attack serves as a crucial reminder for both individuals and organizations to reevaluate their security measures.”
Meanwhile, Fortinet FortiGuard Labs recently disclosed details about a malicious PyPI package called zlibxjson, which had capabilities to steal sensitive information, such as Discord tokens, browser cookies, and stored passwords. The package was downloaded 602 times before being removed from PyPI.
“These actions can result in unauthorized access to user accounts and the exfiltration of personal data, clearly marking the software as malicious,” said security researcher Jenna Wang.



