Malware Linked to North Korea Targets Developers on Windows, Linux, and macOS
The cybercriminals behind an ongoing malware campaign targeting software developers have introduced new malware and tactics, broadening their reach to include Windows, Linux, and macOS platforms.
This activity, known as DEV#POPPER and attributed to North Korea, has been observed targeting victims in South Korea, North America, Europe, and the Middle East.
In a report shared with The Hacker News, Securonix researchers Den Iuzvyk and Tim Peck described the attack as “a sophisticated form of social engineering, designed to manipulate individuals into revealing confidential information or taking actions they normally wouldn’t.”
DEV#POPPER is the name given to an active malware campaign that deceives software developers into downloading malicious software hosted on GitHub, disguised as part of a job interview process. This campaign shows similarities to another operation tracked by Palo Alto Networks Unit 42, known as Contagious Interview.
Earlier this month, evidence surfaced indicating that the campaign was more extensive and cross-platform, with researchers discovering artifacts targeting both Windows and macOS, delivering an updated version of malware known as BeaverTail.
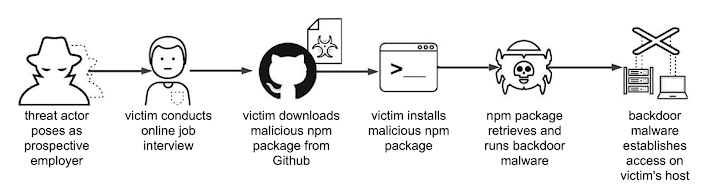
The attack chain documented by Securonix follows a consistent pattern, where threat actors impersonate interviewers for a developer position and prompt candidates to download a ZIP archive file as part of a coding assignment.
Included in the archive is an npm module that, once installed, triggers the execution of an obfuscated JavaScript file (known as BeaverTail). This script identifies the operating system on which it’s running and connects to a remote server to exfiltrate valuable data.
Additionally, the malware can download further payloads, such as a Python backdoor named InvisibleFerret, which is designed to collect detailed system metadata, access browser cookies, execute commands, upload and download files, and log keystrokes and clipboard content.
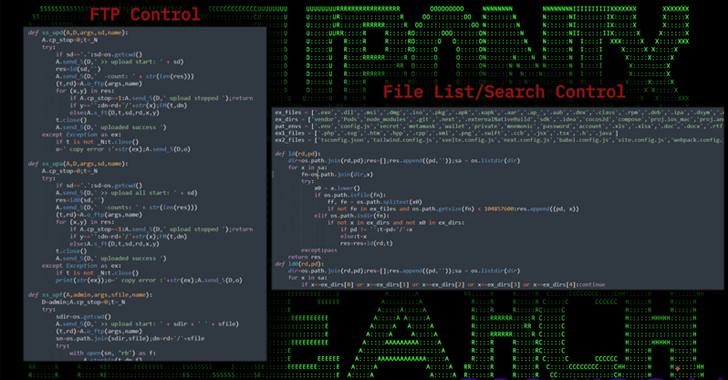
Recent samples have shown new features, including enhanced obfuscation techniques, the use of AnyDesk remote monitoring and management (RMM) software for persistence, and improvements to the FTP mechanism used for data exfiltration.
The Python script also serves as a channel for running another script that targets web browsers like Google Chrome, Opera, and Brave to steal sensitive information across different operating systems.
“This sophisticated expansion of the original DEV#POPPER campaign continues to utilize Python scripts for a multi-stage attack focused on exfiltrating sensitive data from victims, now with significantly enhanced capabilities,” the researchers noted.
These findings coincide with a report from Recorded Future, which revealed that North Koreans continue to use foreign technology—including devices from Apple, Samsung, Huawei, and Xiaomi, as well as social media platforms like Facebook, X, Instagram, WeChat, LINE, and QQ—to access the internet despite strict sanctions.
Another notable shift in user behavior in North Korea involves the increased use of virtual private networks (VPNs) and proxies to bypass censorship and surveillance, along with the adoption of antivirus software from McAfee, suggesting that the country is not as isolated as it appears.
“Despite the sanctions, North Korea continues to import foreign technology, often through its trade relationships with China and Russia,” the report stated. “This indicates a growing awareness of operational security among users who are keen to avoid detection by the regime.”