Mandrake Spyware Resurfaces in Google Play Store Apps After a Two-Year Interval

A new variant of the sophisticated Mandrake spyware has been identified in five apps on the Google Play Store, where it evaded detection for two years.
According to Kaspersky’s report on Monday, these apps were downloaded over 32,000 times before being removed. The majority of these downloads came from countries including Canada, Germany, Italy, Mexico, Spain, Peru, and the U.K.
Researchers Tatyana Shishkova and Igor Golovin noted that the latest version of Mandrake incorporates advanced obfuscation and evasion techniques. This includes relocating malicious functions to obscured native libraries, using certificate pinning for command-and-control (C2) communications, and conducting extensive tests to determine if the spyware is running on a rooted device or within an emulated environment.
Mandrake was initially identified by Bitdefender in May 2020, with its stealthy infection method dating back to 2016.
The new versions use OLLVM for further obfuscation and employ various sandbox evasion and anti-analysis techniques to avoid detection by malware analysts.
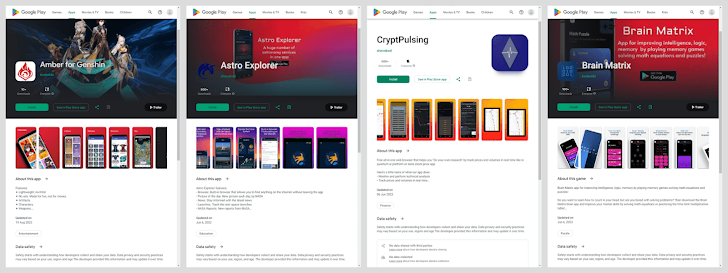
The affected apps are:
- AirFS (com.airft.ftrnsfr)
- Amber (com.shrp.sght)
- Astro Explorer (com.astro.dscvr)
- Brain Matrix (com.brnmth.mtrx)
- CryptoPulsing (com.cryptopulsing.browser)
These apps operate in three stages: first, a dropper installs a loader that downloads and decrypts the core malware component from a command-and-control server.
The second-stage payload of Mandrake spyware is designed to gather information about the device’s connectivity, installed apps, battery level, external IP address, and current Google Play version. Additionally, it has the capability to erase its core module and request permissions to overlay screens and operate in the background.
The third stage extends its functionality to load a specific URL in a WebView, initiate remote screen sharing, and record the device’s screen. These actions aim to capture user credentials and deploy additional malware.
Researchers noted that with Android 13’s introduction of the ‘Restricted Settings’ feature, sideloaded apps are barred from directly requesting dangerous permissions. Mandrake circumvents this by using a ‘session-based’ package installer during installation.
The Russian security firm characterized Mandrake as an example of a constantly evolving threat, which adapts its methods to overcome defense mechanisms and avoid detection.
This evolution underscores the attackers’ sophisticated techniques and the fact that stricter app controls only lead to more advanced and harder-to-detect threats infiltrating official app stores.
In response, Google stated that it is continually enhancing Google Play Protect to address new malicious apps and improve its live threat detection capabilities against obfuscation and evasion techniques.
“Google Play Protect automatically defends against known versions of this malware on Android devices with Google Play Services,” a Google spokesperson explained. “It can warn users or block apps with malicious behavior, even if they come from outside the Play Store.”