New Android Banking Trojan BingoMod Steals Funds and Erases Devices
Cybersecurity researchers have identified a new Android remote access trojan (RAT) named BingoMod that not only conducts unauthorized money transfers from compromised devices but also erases the devices to remove traces of the malware.
Italian cybersecurity firm Cleafy discovered BingoMod in late May 2024 and noted that the malware is still actively being developed. They suspect a Romanian-speaking threat actor is behind it, based on Romanian language comments found in the source code of earlier versions.
“BingoMod represents a new generation of mobile RATs, with its remote access features enabling threat actors to perform Account Takeovers (ATO) directly from the infected device, utilizing the on-device fraud (ODF) technique,” said researchers Alessandro Strino and Simone Mattia.
This technique has also been seen in other Android banking trojans, including Medusa (also known as TangleBot), Copybara, and TeaBot (also known as Anatsa).
Like the BRATA trojan, BingoMod features a self-destruction mechanism designed to erase evidence of fraudulent transactions from the infected device, complicating forensic investigations. While this mechanism only affects the device’s external storage, it is believed that the remote access capabilities may allow for a full factory reset.
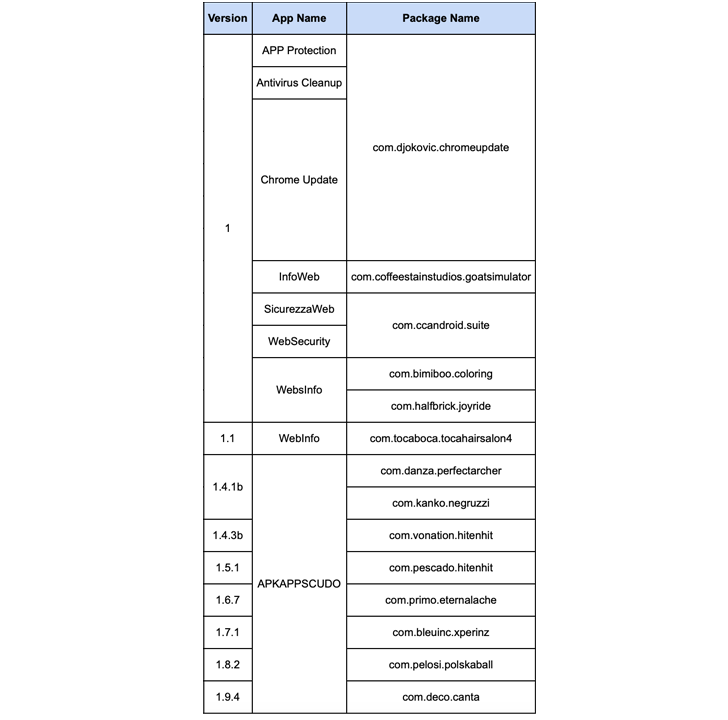
Some of the identified apps disguise themselves as antivirus tools or updates for Google Chrome. Once installed, they prompt users to grant accessibility services permissions, which are then used to carry out malicious activities.
These actions include executing the primary payload, locking the user out of the main screen to gather device information, and sending that data to a server controlled by the attacker. The apps also exploit the accessibility services API to capture sensitive information displayed on the screen, such as credentials and bank account balances, and gain permission to intercept SMS messages.
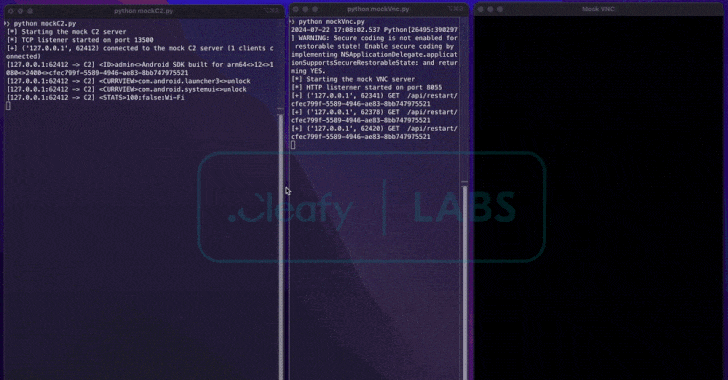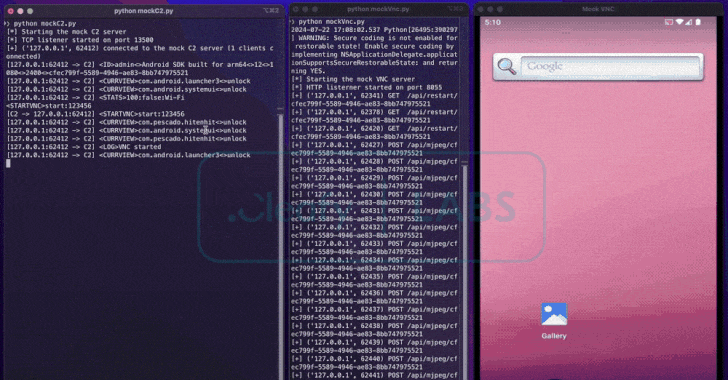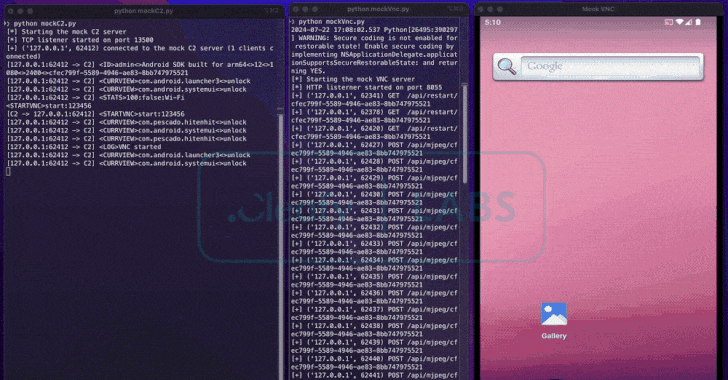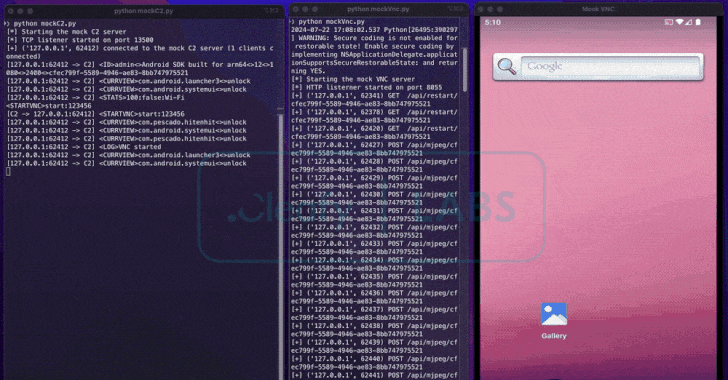
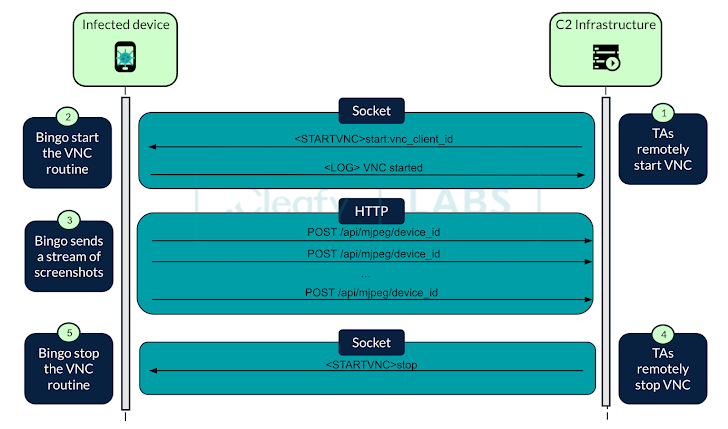
To facilitate money transfers directly from compromised devices, BingoMod establishes a socket-based connection with its command-and-control (C2) server, allowing it to receive up to 40 remote commands. These commands enable the malware to take screenshots using Android’s Media Projection API and interact with the device in real-time.
This setup means that the on-device fraud (ODF) technique requires a live operator to manually execute money transfers of up to €15,000 (~$16,100) per transaction, rather than using an Automated Transfer System (ATS) for large-scale financial fraud.
Additionally, the malware employs code obfuscation to avoid detection and has the capability to uninstall arbitrary apps from the compromised device, suggesting that the malware creators favor straightforward methods over more complex features.
The researchers also noted that BingoMod includes phishing features through Overlay Attacks and fake notifications. Unusually, these overlay attacks are not triggered by specific target apps but are instead activated directly by the malware operator.