New Cyberattack Targets Chinese-Speaking Businesses Using Cobalt Strike Payloads
Chinese-speaking users are being targeted by a “highly organized and sophisticated attack” campaign that appears to use phishing emails to infect Windows systems with Cobalt Strike payloads.
According to Securonix researchers Den Iuzvyk and Tim Peck, “The attackers were able to move laterally, establish persistence, and remain undetected within the systems for over two weeks.”
The covert campaign, dubbed SLOW#TEMPEST and not linked to any known threat actor, begins with malicious ZIP files. When extracted, these files initiate an infection chain that leads to the deployment of a post-exploitation toolkit on compromised systems.
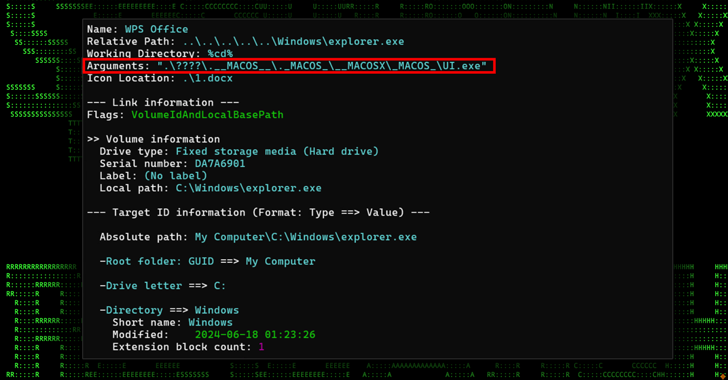
Included in the ZIP archive is a Windows shortcut (LNK) file disguised as a Microsoft Word document named “违规远程控制软件人员名单.docx.lnk,” which translates to “List of people who violated the remote control software regulations.”
Given the nature of the lure files, it’s likely that the attack targets specific Chinese business or government sectors that deal with “remote control software regulations,” the researchers noted.
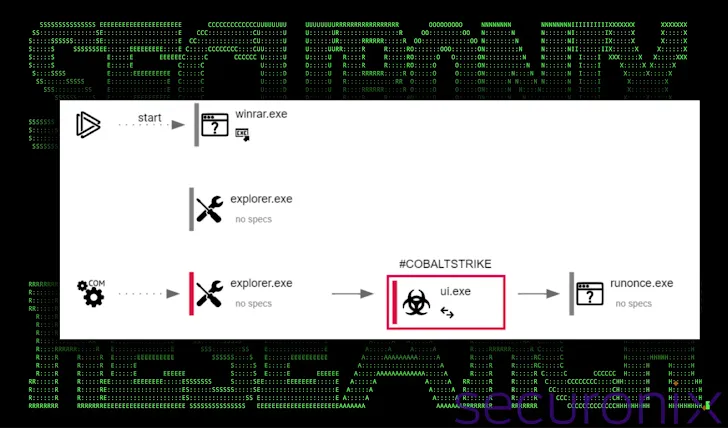
The LNK file launches a legitimate Microsoft binary (“LicensingUI.exe”) which then uses DLL side-loading to execute a malicious DLL (“dui70.dll”). These files are found in a directory within the ZIP archive called “\其他信息.__MACOS__._MACOS___MACOSX_MACOS_.” This marks the first reported instance of DLL side-loading via LicensingUI.exe.
The DLL functions as a Cobalt Strike implant, providing persistent and stealthy access to the infected system and establishing a connection with a remote server (“123.207.74[.]22”).
This remote access enabled the attackers to carry out various activities, including deploying additional payloads for reconnaissance and setting up proxied connections.
Additionally, the attack sets up a scheduled task to run a malicious executable named “lld.exe,” which executes arbitrary shellcode directly in memory, minimizing traces on the disk.
“The attackers further concealed their presence in compromised systems by manually elevating the privileges of the built-in Guest user account,” the researchers reported.
“This account, usually disabled and with limited privileges, was upgraded to a powerful access point by adding it to the critical administrative group and assigning it a new password. This backdoor enables the attackers to maintain access to the system with minimal detection, as the Guest account is typically less monitored than other user accounts.”
The unidentified threat actor then moved laterally across the network using Remote Desktop Protocol (RDP) and credentials extracted via the Mimikatz password extraction tool. They set up remote connections to their command-and-control (C2) server from each compromised machine.
In the post-exploitation phase, the attackers executed various enumeration commands and used the BloodHound tool for Active Directory (AD) reconnaissance. The gathered data was exfiltrated in a ZIP archive.
Connections to China are reinforced by the fact that all C2 servers are hosted in China by Shenzhen Tencent Computer Systems Company Limited. Additionally, most of the artifacts related to the campaign originated from China.
“Although there is no concrete evidence linking this attack to any known APT groups, it is likely orchestrated by a skilled threat actor experienced with advanced exploitation frameworks like Cobalt Strike and a range of other post-exploitation tools,” the researchers concluded.
“The campaign’s complexity is apparent in its systematic approach to initial compromise, persistence, privilege escalation, and lateral movement across the network.”