New Malware Disguised as Palo Alto VPN Targets Middle East Users
Cybersecurity researchers have uncovered a new campaign potentially targeting users in the Middle East through malware disguised as Palo Alto Networks’ GlobalProtect VPN tool.
According to Trend Micro researcher Mohamed Fahmy, “The malware poses a significant threat to targeted organizations by executing remote PowerShell commands, downloading and exfiltrating files, encrypting communications, and bypassing sandbox solutions.”
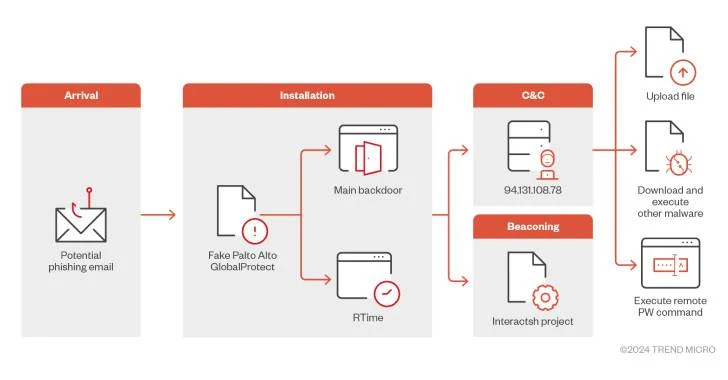
This advanced malware operates in a two-stage process, establishing connections to command-and-control (C2) infrastructure that mimics a legitimate company VPN portal. This allows threat actors to carry out their operations without raising suspicion.
The initial method of intrusion remains unclear, but it is suspected that phishing techniques are used to trick users into believing they are installing the legitimate GlobalProtect agent. The campaign has not yet been linked to any specific threat actor or group.
The attack begins with a setup.exe file that installs a primary backdoor component, GlobalProtect.exe, which starts a beaconing process to notify the operators of the malware’s status.
The first-stage executable also deploys two configuration files, RTime.conf and ApProcessId.conf, which are used to exfiltrate system information—such as the victim’s IP address, operating system details, username, machine name, and sleep time sequence—to a C2 server (94.131.108[.]78).
Fahmy highlighted that the malware employs evasion techniques to bypass behavioral analysis and sandbox detection by verifying the process file path and specific files before executing the main code.
The backdoor is capable of uploading files, downloading additional payloads, and executing PowerShell commands, with beaconing to the C2 server facilitated by the Interactsh open-source project.
“The malware then switches to a newly registered URL, ‘sharjahconnect,’ which likely refers to the U.A.E. emirate of Sharjah, mimicking a legitimate VPN portal for a U.A.E.-based company,” Fahmy explained.
This strategy is designed to blend the malware’s activities with expected regional network traffic, enhancing its ability to evade detection.