North Korean Hackers Transition from Cyber Espionage to Ransomware Attacks
A North Korean-affiliated threat actor renowned for its cyber espionage activities has increasingly shifted towards financially-driven attacks involving ransomware, distinguishing it from other nation-state hacking groups associated with North Korea.
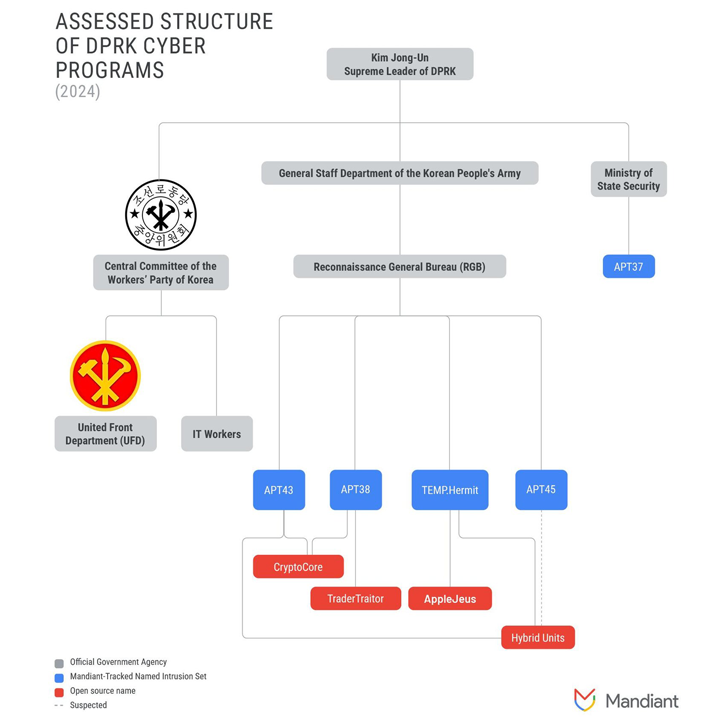
Tracked by Google-owned Mandiant under the new designation APT45, this group has been identified with several aliases, including Andariel, Nickel Hyatt, Onyx Sleet (formerly Plutonium), Silent Chollima, and Stonefly.
“APT45 is a long-established and moderately advanced North Korean cyber operator known for espionage campaigns dating back to 2009,” stated researchers Taylor Long, Jeff Johnson, Alice Revelli, Fred Plan, and Michael Barnhart. “This group has frequently targeted critical infrastructure.”
APT45, along with APT38 (also known as BlueNoroff), APT43 (also known as Kimsuky), and Lazarus Group (also known as TEMP.Hermit), operates under North Korea’s Reconnaissance General Bureau (RGB), the country’s top military intelligence agency.
APT45 is particularly associated with the deployment of ransomware families such as SHATTEREDGLASS and Maui, which targeted organizations in South Korea, Japan, and the U.S. during 2021 and 2022. Details about SHATTEREDGLASS were reported by Kaspersky in June 2021.
Mandiant suggested that APT45 might be engaging in financially-driven cybercrime not only to support its own activities but also to fund other North Korean state objectives.
The group also employs a notable backdoor known as Dtrack (also referred to as Valefor and Preft), which was first identified in a cyberattack on the Kudankulam Nuclear Power Plant in India in 2019. This incident is among the few publicly documented cases of North Korean cyber actors targeting critical infrastructure.
“APT45 is among the longest-running cyber operators from North Korea, and its activities reflect the regime’s shifting geopolitical priorities. Although the group initially focused on traditional cyber espionage against governmental and defense targets, its operations have expanded to include sectors like healthcare and agricultural science,” Mandiant noted.
“As North Korea increasingly relies on its cyber operations as a tool of national power, the actions of APT45 and other North Korean cyber units likely mirror the evolving priorities of the country’s leadership.”
In a related development, security training firm KnowBe4 revealed it was deceived into hiring a North Korean IT worker as a software engineer. This individual used a stolen U.S. identity and manipulated their appearance with artificial intelligence (AI).
“The IT worker, backed by a state-supported criminal network, used a stolen U.S. identity to participate in multiple rounds of video interviews and circumvented typical background checks used by companies,” KnowBe4 explained.
This individual, believed to be part of the Workers’ Party of Korea’s Munitions Industry Department, has a history of applying for positions with U.S.-based firms while physically located in China or Russia, and accessing systems remotely via company-issued laptops from a “laptop farm.”
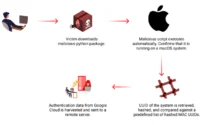
KnowBe4 detected suspicious activity on the Mac workstation sent to this individual on July 15, 2024, at 9:55 p.m. EST. This activity included tampering with session history files, transferring potentially harmful files, and executing malicious software, with the malware being downloaded using a Raspberry Pi.

Twenty-five minutes later, the Florida-based cybersecurity firm reported that it had contained the compromised device. There was no indication that the attacker had accessed sensitive data or systems without authorization.
“The deception involves these individuals actually performing the work, receiving substantial compensation, and channeling a significant portion of their earnings to North Korea to support its illicit programs,” said Stu Sjouwerman, CEO of KnowBe4.
“This incident underscores the urgent need for more rigorous vetting procedures, ongoing security monitoring, and better collaboration between HR, IT, and security teams to defend against advanced persistent threats.”
For more update’s, stay connected with us