PEAKLIGHT Downloader Used in Attacks on Windows Systems Through Malicious Movie Downloads
Cybersecurity researchers have identified a newly discovered dropper that acts as a gateway for deploying subsequent malware stages, ultimately aiming to infect Windows systems with information stealers and loaders.
“This memory-resident dropper decrypts and runs a PowerShell-based downloader,” stated Mandiant, a subsidiary of Google. This downloader, known as PEAKLIGHT, is tracked by the researchers.
The malware strains distributed through this method include Lumma Stealer, Hijack Loader (also known as DOILoader, IDAT Loader, or SHADOWLADDER), and CryptBot, all of which operate under a malware-as-a-service (MaaS) model.
The attack chain begins with a Windows shortcut (LNK) file, which is delivered through drive-by download techniques—such as when users search for movies on search engines. These LNK files are hidden within ZIP archives, which are falsely presented as pirated movies.
The LNK file then connects to a content delivery network (CDN) that hosts an obfuscated memory-only JavaScript dropper. This dropper executes the PEAKLIGHT PowerShell downloader script on the target system, which subsequently contacts a command-and-control (C2) server to retrieve additional malicious payloads.
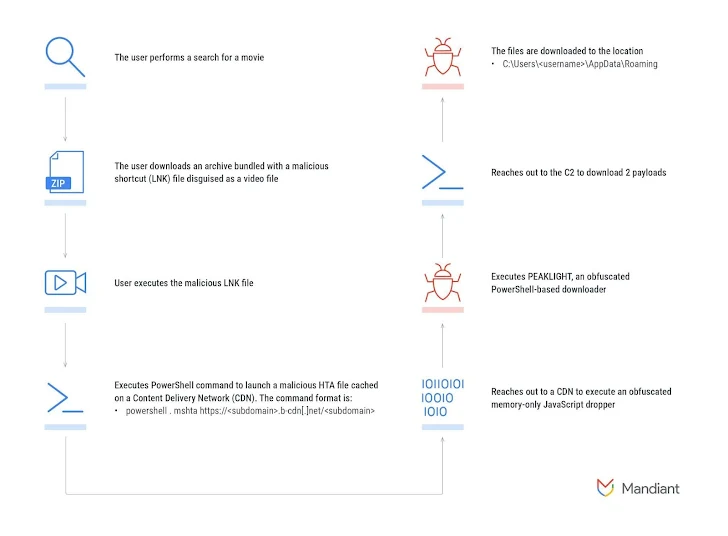
Mandiant reported discovering various versions of LNK files, some of which use asterisks (*) as wildcards to execute the legitimate mshta.exe binary, allowing malicious code (the dropper) to run discreetly from a remote server.
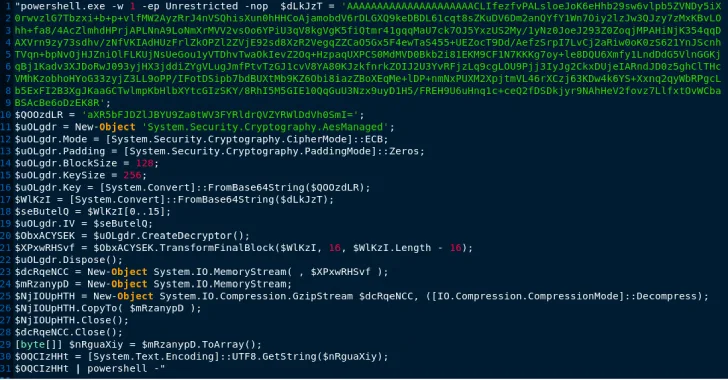
Similarly, the droppers have been found to contain PowerShell payloads encoded in both hexadecimal and Base64 formats, which are eventually unpacked to execute PEAKLIGHT. This downloader is designed to deliver additional malware onto compromised systems while also downloading a legitimate movie trailer, likely as a decoy.
“PEAKLIGHT is an obfuscated PowerShell-based downloader that operates within a multi-stage execution chain, checking for the presence of ZIP archives in specific file paths,” explained Mandiant researchers Aaron Lee and Praveeth D’Souza.
“If the archives are absent, the downloader contacts a CDN site to retrieve the remote archive file and save it to disk.”
This revelation coincides with Malwarebytes’ report on a malvertising campaign that uses fake Google Search ads for Slack, a business communication platform, to redirect users to counterfeit websites hosting malicious installers. These installers ultimately lead to the deployment of a remote access trojan known as SectopRAT.



