Thai Officials Targeted in Yokai Backdoor Attack Exploiting DLL Side-Loading

Thai government officials have been targeted in a new cyber campaign that employs DLL side-loading to deploy an undocumented backdoor known as Yokai.
“The threat actors appear to focus on Thai officials based on the nature of the bait used,” said Nikhil Hegde, senior engineer at Netskope’s Security Efficacy team, in a statement to The Hacker News. However, Hegde noted that the Yokai backdoor could potentially be used against any target.
The attack begins with a RAR archive containing two Windows shortcut files named in Thai, which translate to “United States Department of Justice.pdf” and “United States government requests international cooperation in criminal matters.docx.”
Although the initial method of delivering the archive remains unclear, Hegde suggested spear-phishing as the likely vector due to the nature of the bait and the use of RAR files, which are commonly attached to phishing emails.
When the shortcut files are executed, they open decoy PDF and Word documents while secretly dropping a malicious executable in the background. The bait documents reference Woravit Mektrakarn, a Thai national wanted in the U.S. for the 2003 murder of a Mexican immigrant. Mektrakarn is alleged to have fled to Thailand.
The malicious executable drops three additional files: a legitimate binary from the iTop Data Recovery application (“IdrInit.exe”), a rogue DLL (“ProductStatistics3.dll”), and a DATA file containing attacker-supplied information. The legitimate binary is then exploited to sideload the malicious DLL, resulting in the deployment of the Yokai backdoor.
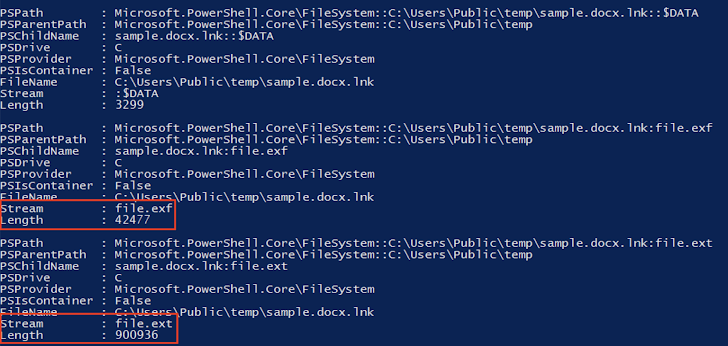
Yokai establishes persistence on the infected system and connects to its command-and-control (C2) server to receive commands. These commands enable it to launch cmd.exe and execute shell commands on the compromised host.
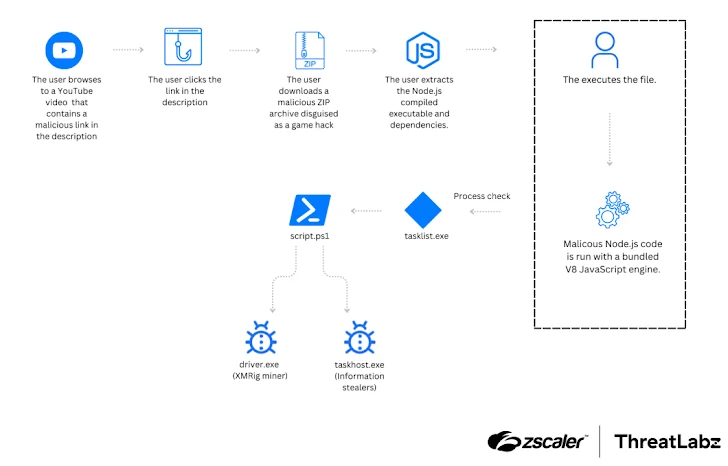
Meanwhile, Zscaler ThreatLabz has identified another malware campaign using Node.js-compiled executables for Windows to distribute cryptocurrency miners and information-stealing malware, including XMRig, Lumma, and Phemedrone Stealer. The malicious programs, collectively referred to as NodeLoader, are delivered through deceptive tactics.
The attackers embed malicious links in YouTube video descriptions, redirecting users to MediaFire or fake websites that offer a ZIP archive disguised as video game cheats. Once downloaded, the archive contains NodeLoader, which executes a PowerShell script to deploy the final-stage malware.
“NodeLoader utilizes a module called sudo-prompt, an open-source tool available on GitHub and npm, to escalate privileges,” Zscaler explained. The campaign relies on social engineering and anti-detection measures to deliver NodeLoader without raising suspicion.
This development coincides with a rise in phishing attacks delivering the commercially available Remcos RAT. Attackers have updated their infection methods, using Visual Basic Script (VBS) files and Office Open XML documents to initiate multi-stage malware delivery processes.
In one attack scenario, running the VBS file triggers a heavily obfuscated PowerShell script, which downloads additional payloads. This process ultimately leads to the injection of the Remcos RAT into RegAsm.exe, a legitimate Microsoft .NET executable.
In another variation, attackers use an Office Open XML document to load an RTF file that exploits CVE-2017-11882, a remote code execution vulnerability in Microsoft Equation Editor. This flaw is used to retrieve a VBS file, which then executes a PowerShell script to inject the Remcos RAT directly into the memory of RegAsm.exe.
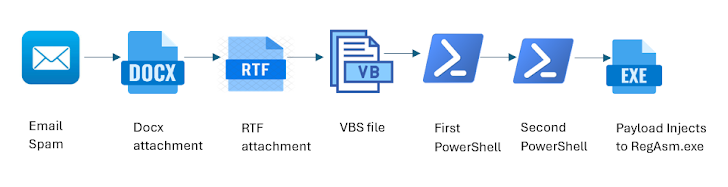
Both techniques are designed to avoid writing files to disk, instead loading them directly into legitimate processes to bypass detection by security tools.
“With this remote access trojan continuing to target users through phishing emails and malicious attachments, the importance of adopting proactive cybersecurity measures has never been greater,” noted researchers from McAfee Labs.